Most serious errors and security threats in software originate from pointer overflows, pointer overwrite and memory miss-management. This causes invalid/un-authorised memory addresses to be interpreted as valid references which in turn results in applications accessing restricted or unavailable memory. Such access can be exploited by an attacker to inject malicious data into memory, take control …
Category: Tech Blog
Improving Yocto Build Time
Yocto is an excellent distribution builder, however building any Linux distribution from scratch is resource intensive and may take a frustrating long time. This blog posts examines some of the most common techniques that can be used to reduce build times (and resource use). Downloads During a build, bitbake fetches source code from the internet …
2 Second Linux Boot on i.MX8
Earlier this year we we wrote a blog post that looked at the steps required to enable hardware accelerated image classification on an i.MX8 based Coral Dev Board. We created a Linux ‘Tux mascot detector’ that was able to detect if an object placed in front of a camera was the Tux mascot or something …
Understanding why USB Isochronous Bandwidth Errors Occur
A recent customer asked us to make sense of USB bandwidth errors that prevented them from streaming multiple USB audio and video streams simultaneously. Their GStreamer pipelines would fail and a “uvcvideo: Failed to submit URB 0 (-28).” message would be seen in dmesg. The interesting part is that the errors would only occur if …
PCIe DMA Attack against a secured Jetson Nano (CVE-2022-21819)
Congratulations! Your Jetson Nano (T210) product is finished and ready to ship worldwide. Secure boot is enabled, Linux and it’s bootloaders are locked down and the file system holding your precious IP is encrypted. Even JTAG is disabled with an OTP (One-Time-Programmable) security fuse. Yet, lurking in the Jetson Nano’s Linux kernel is a PCIe …
Edge AI: Image Classification on a Coral Dev Board
There are many benefits in moving artificial intelligence from the cloud to the local device – these include improvements to privacy, security, speed and reliability. However, device local AI (Edge AI and Endpoint AI) has only become possible thanks to improvements in both the computing abilities of embedded devices and improvements in the field of …
Reducing Boot Time with systemd
It’s no surprise that systemd has become the init system of choice for both embedded and desktop Linux distributions – it’s modern, packed full of features and is able to replace an ever increasing number of ancient utilities and daemons. When compared to it’s predecessor (SysVinit) – it also provides a much greater scope for …
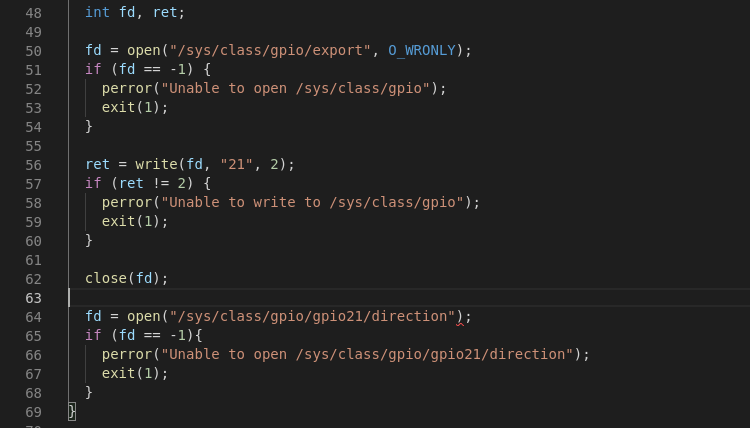
Stop using /sys/class/gpio – it’s deprecated
The well known /sys/class/gpio interface has been around since version 2.6.27 of the kernel – way back in 2008. It provides an easy to use, file-based means of accessing GPIO from user-space. In the embedded Linux space it’s commonly used by applications to directly interact with hardware and most engineers can probably recount times where …
Linux Ethernet phy-mode Bindings Explained
Whilst on the user side Ethernet is a pretty easy to grasp standard, most people’s experience is either the now ubiquitous 8pin RJ45 interface or at a higher end of the speed scale possibly SPF/QSFP and fibre optic links. However on the other side of the simple connector, inside the box, there are a multitude …
Keeping Track of Time with Systemd
Nearly all smart devices obtain and keep track of time – it’s something that ‘just works’ and something which we often take for granted. Yet under-the-hood there is a surprising amount of complexity – software needs to obtain an accurate external source of time (e.g. NTP), it needs to handle drift and gradual synchronisation between …