Yocto is so widely used because of the many benefits it provides to engineers that wish to build customised Linux distributions. However, it does have pain points. One such pain point relates to the difficulty of getting a Yocto development environment setup in the first place – this often involves using third-party tools such as …
Category: Yocto
Linux Yocto layer for the ARM Morello board
We have recently developed and now maintain the meta-morello Yocto layer for ARM’s Morello board which has now became part of the official software stack. The layer is capable of providing the firmware image that goes on the SD card and a bootable image with Linux that goes on the USB stick, these two images …
Self-installing Yocto Image from a USB drive
We are all familiar with the process of installing a desktop operating system onto a PC; simply insert the installation media, typically a USB stick, and boot the device. A minimal version of the OS then runs to perform the process of partitioning discs and installing the full OS. Yocto also has the ability to …
ARM Morello with Linux
ARM has recently made their Morello development on the Linux kernel public and since we are lucky enough to have access to the Morello board we decided to give this a spin. This is in contrast to our last blog post which used an Android stack and ran in a simulator. Kernel development in the …
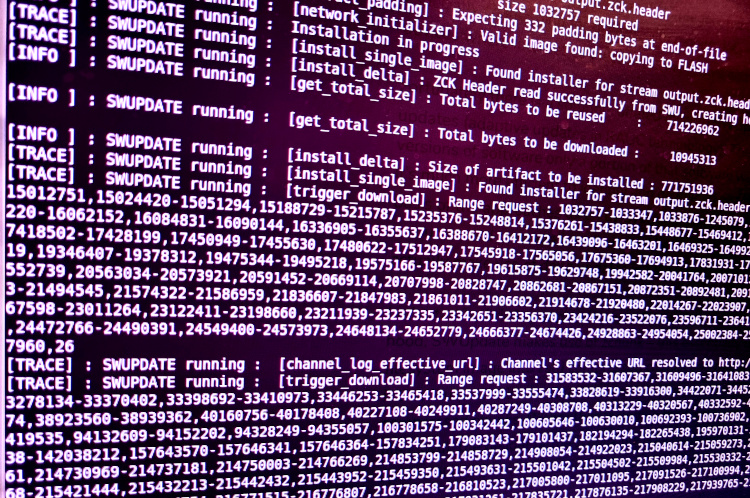
Delta OTA Update with SWUpdate
With the complexity and dependence on software ever growing, it’s crucial to be able to perform over-the-air (OTA) updates to devices to provide fixes, features and patches for security vulnerabilities. However, a combination of cheap storage and complex software stacks has resulted in an increase in the size of software distributions thus requiring devices to …
Improving Yocto Build Time
Yocto is an excellent distribution builder, however building any Linux distribution from scratch is resource intensive and may take a frustrating long time. This blog posts examines some of the most common techniques that can be used to reduce build times (and resource use). Downloads During a build, bitbake fetches source code from the internet …
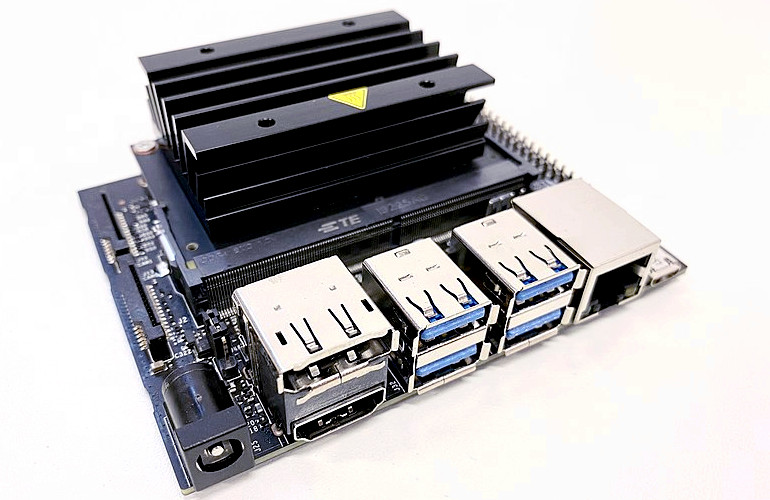
Diving into the NVIDIA Jetson Nano Boot Process
The NVIDIA Jetson has become one of the platforms of choice for experimenting with Vision based AI, Robotics, Machine learning and a host of other subjects. It’s marriage of high performance Arm cores with NVIDIA’s own advanced GPU engines makes it both incredibly powerful and very accessible. The Jetson Nano Developer Kit is one of …
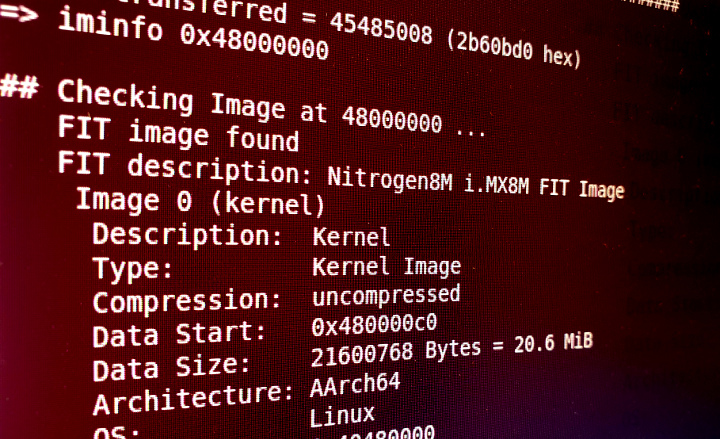
Flattened uImage Tree (FIT) Images
You’re probably familiar with the steps required to boot Linux from U-Boot: you first load several binaries into memory, perhaps a device tree, a kernel, maybe even an initrd. You then invoke a command such as bootm or booti with arguments providing memory addresses for the binaries you’ve just loaded. However there is a much …
Yocto Security Hardening: Security Flags
In our internet connected world, which relies on a growing volume of software – it’s crucial that new products are created with security in mind. Yet much of the software we create or depend on is written with memory-unsafe languages such as C and C++ – It’s a worrying fact given that 70% of all …
Yocto Security Hardening: CVEs
The volume and complexity of the software running in embedded devices is not only astonishing but ever increasing – yet each additional line of code has the potential to introduce a security vulnerability. An attacker may only need to exploit one single vulnerability for a bad outcome to occur. Therefore the obvious way to reduce …