In our previous blog post, we explored securing keys and certificates with Toradex’s recently launched i.MX 95 Verdin Evaluation Kit. We also demonstrated how to build and customise a Yocto reference image for the i.MX 95 Verdin EVK, leveraging OP-TEE and PKCS#11 which you can find here. Another essential aspect of achieving a high level …
Category: Tech Blog
Securing Keys and Certificates with i.MX 95 Verdin EVK using PKCS#11 with OP-TEE
Toradex recently launched the i.MX 95 Verdin Evaluation Kit, designed to accelerate next-generation Edge AI, automotive, industrial and medical applications all of which are industries that require high levels of security. An essential aspect of achieving a high level of security is the management and storage of cryptographic keys. This is crucial for authenticating to …
Exploiting a Buffer Overflow Vulnerability for Remote Code Execution in Nginx
Protecting devices from malicious use is often a cat-and-mouse game between security researchers identifying software vulnerabilities (CVEs) and product-makers patching them before attackers can exploit them. As a result, devices can no longer be developed, shipped and forgotten. Instead, manufacturers must commit to keeping those devices up to date and free from critical vulnerabilities for …
ETSI EN 303 645: Cyber Security for Consumer Internet of Things
We increasingly rely on internet connected devices in our day-to-day lives, with consumer devices that include door bell cameras, thermostats, children’s toys and home assistants. However the cyber security of these devices doesn’t always live up to the trust we place in them to reliability perform their function and protect our personal data. It’s often …
The Good Penguin speaks at the Embedded Open Source Summit 2024 in Seattle
Earlier this year, our founder Andrew Murray presented a talk at the Embedded Open Source Summit 2024 in Seattle. The talk was about SD cards, their performance and reliability. The synopsis of the talk follows: “The underlying storage of an SD card is NAND flash, which is inherently unreliable, has a limited number of program/erase …
i.MX Code Signing using a YubiHSM 2 Hardware Token from Yubico
Code signing is fairly ubiquitous and is a cryptographic technique for verifying the authenticity of a binary. It is often used as part of the secure boot process of an embedded device where software components of the bootchain are verified by the previous component. For example, the on-chip ROM in a SoC will verify the …
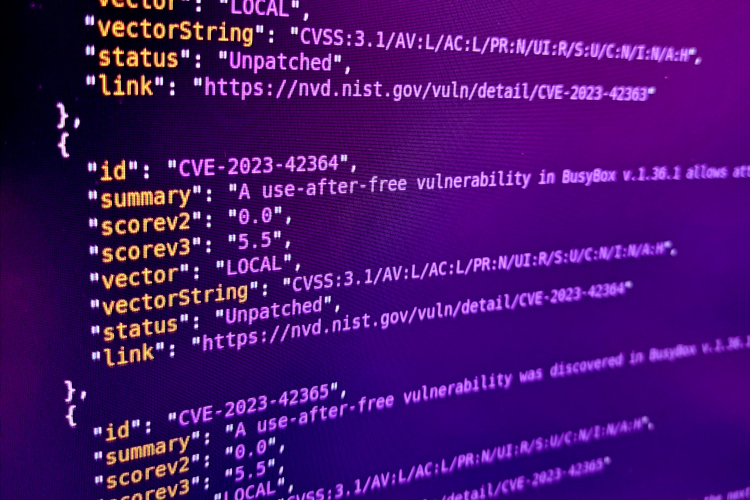
Handling Security Vulnerabilities in Yocto Scarthgap
The latest Long Term Support (LTS) version of Yocto was released last month with the code name “Scarthgap” – presumably named after a mountain pass in the Lake District national park. It promises 4 years of support, meaning regular point releases with security and bug fixes. In the context of increasing regulatory requirements for cyber …
Everything you ought to know (and more) about Yocto’s SDK and Extensible SDK (eSDK)
Yocto is so widely used because of the many benefits it provides to engineers that wish to build customised Linux distributions. However, it does have pain points. One such pain point relates to the difficulty of getting a Yocto development environment setup in the first place – this often involves using third-party tools such as …
The Journey of I/O from Userspace to Device
When a Linux userspace application performs disk I/O – such as writing to an SD card, those requests go through a complex journey across multiple kernel components. These components aim to deliver optimal I/O performance whilst balancing a variety of needs such as latency and fairness. However, when things go wrong, it can be challenging …
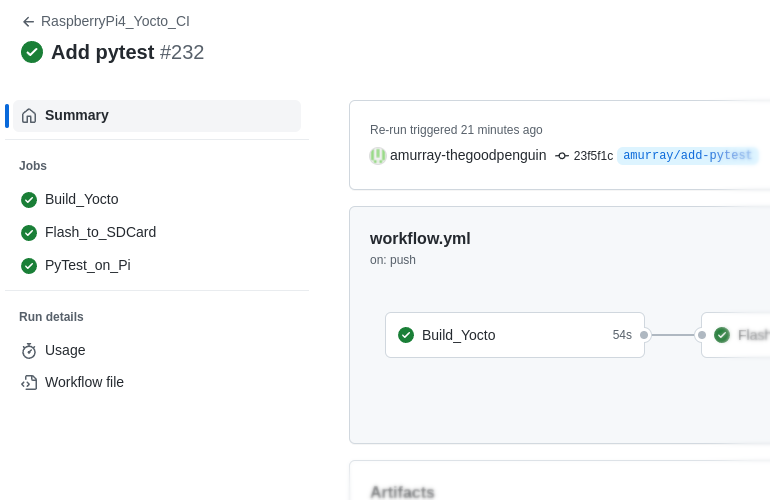
Automated Testing with GitHub Actions, pytest and a Board Farm
When developing software it can be a real challenge to consistently deliver new features on time and without regressions. It can often feel like development gets stuck at the point of trying to get a new release out of the door with mountains of issues suddenly appearing. In an effort to improve development velocity many …