We have recently developed and now maintain the meta-morello Yocto layer for ARM’s Morello board which has now became part of the official software stack. The layer is capable of providing the firmware image that goes on the SD card and a bootable image with Linux that goes on the USB stick, these two images …
Category: Tech Blog
Self-installing Yocto Image from a USB drive
We are all familiar with the process of installing a desktop operating system onto a PC; simply insert the installation media, typically a USB stick, and boot the device. A minimal version of the OS then runs to perform the process of partitioning discs and installing the full OS. Yocto also has the ability to …
SWUpdate, Suricatta and Unreliable Connectivity
Many product makers choose to use the open-source SWUpdate software to provide an off the shelf method of software update for their embedded devices. For internet connected devices this is typically configured in Suricatta daemon mode which allows for SWUpdate to poll for software updates from an update server such as the open-source Eclipse Hawkbit. …
Debugging a Memory Leak in a Large and Complex GStreamer Pipeline
GStreamer is a widely used and comprehensive multimedia framework allowing for the creation of a wide range of multimedia applications. It has become the obvious choice for embedded Linux systems, especially given that these days most BSP vendors choose to provide GStreamer plugins for their media accelerators. It’s ease of use allows you to create …
ARM Morello with Linux
ARM has recently made their Morello development on the Linux kernel public and since we are lucky enough to have access to the Morello board we decided to give this a spin. This is in contrast to our last blog post which used an Android stack and ran in a simulator. Kernel development in the …
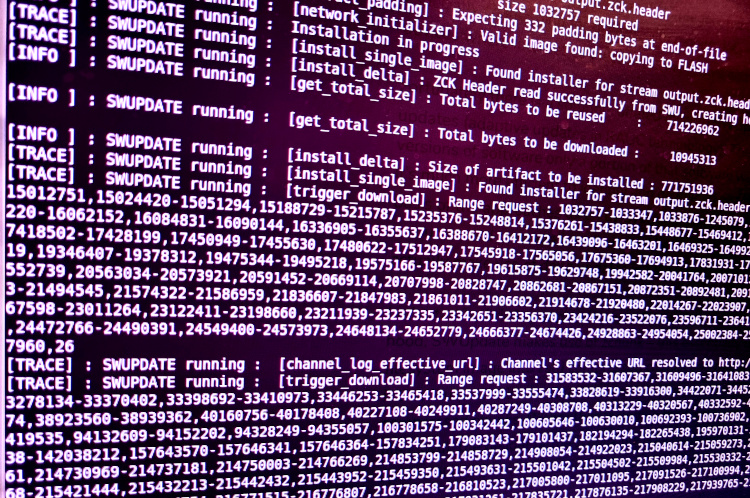
Delta OTA Update with SWUpdate
With the complexity and dependence on software ever growing, it’s crucial to be able to perform over-the-air (OTA) updates to devices to provide fixes, features and patches for security vulnerabilities. However, a combination of cheap storage and complex software stacks has resulted in an increase in the size of software distributions thus requiring devices to …
Baking Android for ARM Morello without Morello
Access to ARM Morello boards is fairly limited at the moment, but we can still explore the new architecture with the help of a Fixed Virtual Platform (FVP) and software stack packages that are available from ARM. In a previous blog post we provided an introduction to Arm Morello and CHERI. In this post we’re …
Introducing Arm Morello and CHERI
Most serious errors and security threats in software originate from pointer overflows, pointer overwrite and memory miss-management. This causes invalid/un-authorised memory addresses to be interpreted as valid references which in turn results in applications accessing restricted or unavailable memory. Such access can be exploited by an attacker to inject malicious data into memory, take control …
Improving Yocto Build Time
Yocto is an excellent distribution builder, however building any Linux distribution from scratch is resource intensive and may take a frustrating long time. This blog posts examines some of the most common techniques that can be used to reduce build times (and resource use). Downloads During a build, bitbake fetches source code from the internet …
2 Second Linux Boot on i.MX8
Earlier this year we we wrote a blog post that looked at the steps required to enable hardware accelerated image classification on an i.MX8 based Coral Dev Board. We created a Linux ‘Tux mascot detector’ that was able to detect if an object placed in front of a camera was the Tux mascot or something …