Yocto is an excellent distribution builder, however building any Linux distribution from scratch is resource intensive and may take a frustrating long time. This blog posts examines some of the most common techniques that can be used to reduce build times (and resource use). Downloads During a build, bitbake fetches source code from the internet …
Tag: Yocto
Edge AI: Image Classification on a Coral Dev Board
There are many benefits in moving artificial intelligence from the cloud to the local device – these include improvements to privacy, security, speed and reliability. However, device local AI (Edge AI and Endpoint AI) has only become possible thanks to improvements in both the computing abilities of embedded devices and improvements in the field of …
Keeping Track of Time with Systemd
Nearly all smart devices obtain and keep track of time – it’s something that ‘just works’ and something which we often take for granted. Yet under-the-hood there is a surprising amount of complexity – software needs to obtain an accurate external source of time (e.g. NTP), it needs to handle drift and gradual synchronisation between …
Diving into the NVIDIA Jetson Nano Boot Process
The NVIDIA Jetson has become one of the platforms of choice for experimenting with Vision based AI, Robotics, Machine learning and a host of other subjects. It’s marriage of high performance Arm cores with NVIDIA’s own advanced GPU engines makes it both incredibly powerful and very accessible. The Jetson Nano Developer Kit is one of …
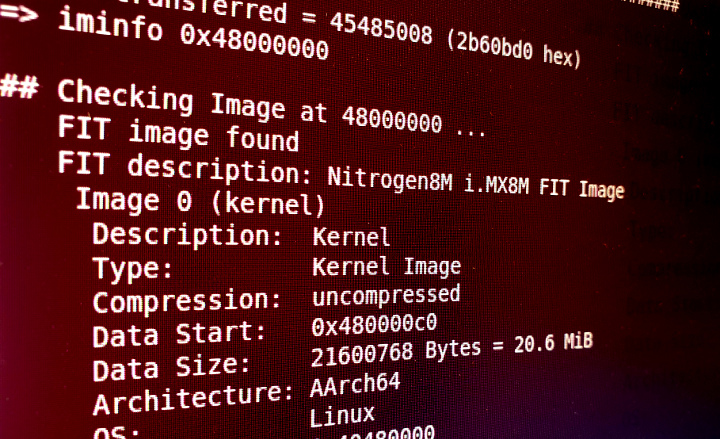
Flattened uImage Tree (FIT) Images
You’re probably familiar with the steps required to boot Linux from U-Boot: you first load several binaries into memory, perhaps a device tree, a kernel, maybe even an initrd. You then invoke a command such as bootm or booti with arguments providing memory addresses for the binaries you’ve just loaded. However there is a much …
Yocto Security Hardening: Security Flags
In our internet connected world, which relies on a growing volume of software – it’s crucial that new products are created with security in mind. Yet much of the software we create or depend on is written with memory-unsafe languages such as C and C++ – It’s a worrying fact given that 70% of all …
Yocto Security Hardening: CVEs
The volume and complexity of the software running in embedded devices is not only astonishing but ever increasing – yet each additional line of code has the potential to introduce a security vulnerability. An attacker may only need to exploit one single vulnerability for a bad outcome to occur. Therefore the obvious way to reduce …