This Xmas the Good Penguin is raising money for The Forever Friends Appeal – the official NHS charity for the Royal United Hospital (RUH) in Bath. The money we raise will go to the newborn intensive care unit (NICU) to provide state-of-the-art treatment, diagnostic equipment, and to support families at one of the most vulnerable …
Author: Andrew Murray
Supporting NAND on SpiStack via the LS1012A’s QuadSPI Controller
We’ve recently provided software support to Analogue & Micro who are developing hardware derived from NXP’s Layerscape FRWY-LS1012A reference design. What we find interesting about this reference design is that for storage it uses an innovative SPI memory known as SpiStack Flash. Essentially it’s a single chip with a quad-SPI interface, but inside are two …
An overview of OpenSBI
Thanks to BeagleBoard.org, we’ve recently received a pre-production beta version of the BeagleV StarLight development board. It’s an affordable Linux platform that’s truly open source with it’s software, hardware design and RISC-V instruction set architecture all made available under free and open licenses. When we booted the board for the first time we noticed some …
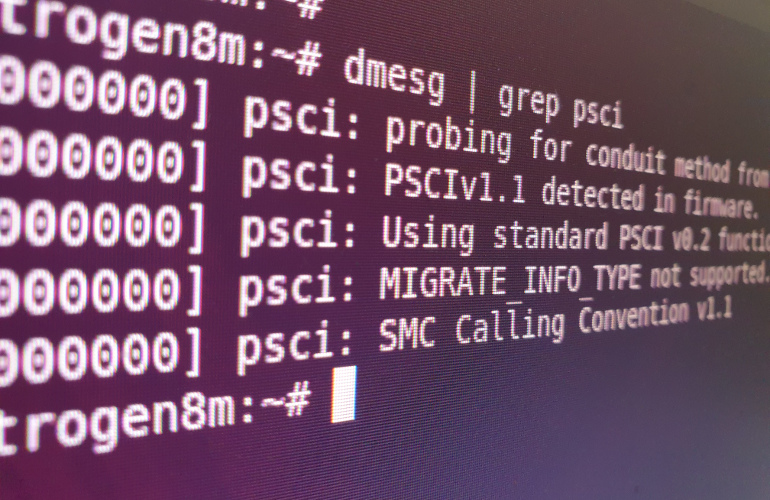
An overview of PSCI
If you boot a 64-bit kernel on an ARMv8-A platform, you’ll probably notice some output relating to PSCI. In this post, we’re going to explore what this is and why it’s there. The Power State Coordination Interface (PSCI) is an ARM standard that describes a software interface for power management between an operating system (not …
5 Serial Automation Gotchas
Automated tests that make use of interactive consoles are commonplace. Whether it’s a Linux console over a serial port or a proprietary CLI over a network socket – they require little in terms of hardware yet give access to lots of functionality. However writing a reliable automated test can be more challenging and time consuming …
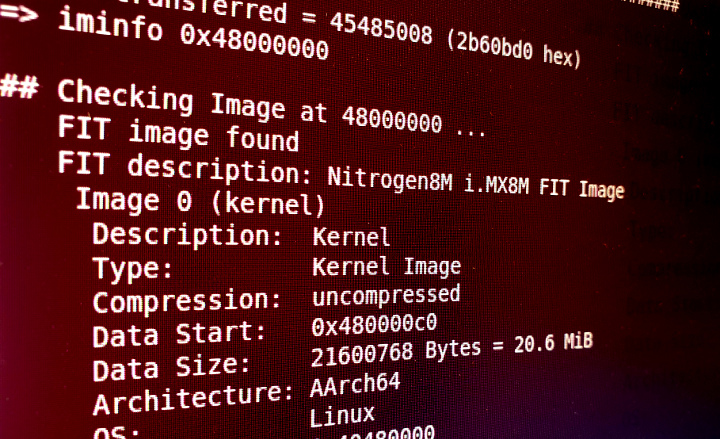
Flattened uImage Tree (FIT) Images
You’re probably familiar with the steps required to boot Linux from U-Boot: you first load several binaries into memory, perhaps a device tree, a kernel, maybe even an initrd. You then invoke a command such as bootm or booti with arguments providing memory addresses for the binaries you’ve just loaded. However there is a much …
Yocto Security Hardening: Security Flags
In our internet connected world, which relies on a growing volume of software – it’s crucial that new products are created with security in mind. Yet much of the software we create or depend on is written with memory-unsafe languages such as C and C++ – It’s a worrying fact given that 70% of all …
Power-failure-tolerant bootloader flashing on eMMC
It’s a widely held misconception that flashing a bootloader on a device in the field is risky. The reason is that if power is removed from the device during update, then the bootloader may only be partially flashed and thus won’t boot. This view is correct for devices that boot from a single location without …
Yocto Security Hardening: CVEs
The volume and complexity of the software running in embedded devices is not only astonishing but ever increasing – yet each additional line of code has the potential to introduce a security vulnerability. An attacker may only need to exploit one single vulnerability for a bad outcome to occur. Therefore the obvious way to reduce …
Booting Linux from Linux with kexec
The Linux kernel feature known as ‘kexec‘ allows you to boot from the currently running kernel into a new kernel – effectively turning a Linux distribution into a feature-rich bootloader. This shouldn’t be confused with virtualisation technologies that allow you to run Linux as a guest. This capability has been around since 2005 (2.6.13) and …